Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
Easterhegg 2026 – Tickets, Merch und mehr
TL;DR: Ein neues Jahr – eine neue Easterhegg. Dieses Jahr findet sie an der Universität Koblenz vom 3. bis zum 6. April statt. Das Motto der Easterhegg dieses Jahr ist „The Bunny is a Lie!“.
Call for ParticipationDamit es ein richtig gutes Event wird, fehlt nur noch deine Einreichung! Wenn ihr euer Fachwissen, die neuesten Entwicklungen in einem eurer Projekte oder vielleicht sogar etwas ganz anderes vorstellen wollt, könnt ihr euren Beitrag noch bis zum 27.2. bei uns einreichen. Wir bereiten gerne die Bühne für euren Beitrag.
Generell solltest du bei deiner Einreichung beachten, dass die Beschreibung sowie der Titel aussagekräftig sind....
Unseen (jh26)

Ein Routenplaner, um Überwachungskameras zu umgehen.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-176-deu-Unseen_hd.mp4
Roll with me (jh26)

Ein Koffer, der einen automatisch verfolgt.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-179-deu-Roll_with_me_hd.mp4
Community Games Library (jh26)

Eine Spielesammlung für die Gemeinschaft.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-181-deu-Community_Games_Library_hd.mp4
Abschlusspräsentation (jh26)

Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-170-deu-Abschlusspraesentation_hd.mp4
WE CREATE SPACE (jh26)
Ein soziales Netzwerk für kreative Menschen.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-178-deu-WE_CREATE_SPACE_hd.mp4
Fächerwahl leicht gemacht (jh26)

Eine Entscheidungshilfe für den Wirrwarr der Kurswahl in der gymnasialen Oberstufe.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-175-deu-Faecherwahl_leicht_gemacht_hd.mp4
Privacy Helper (jh26)

Eine Browsererweiterung, die verhindert, dass persönliche Daten unbeabsichtigt preisgegeben werden.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-180-deu-Privacy_Helper_hd.mp4
Cup-stabilizer (jh26)

Wir stabilisieren deinen Becher.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-174-deu-Cup-stabilizer_hd.mp4
Wie funktioniert ChatGPT? (jh26)
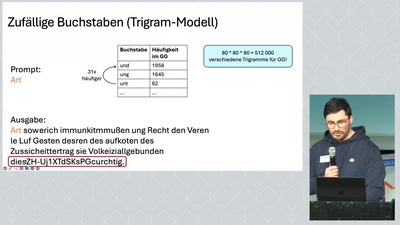
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-177-deu-Wie_funktioniert_ChatGPT_hd.mp4