Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
Introducing the Qubes Admin API
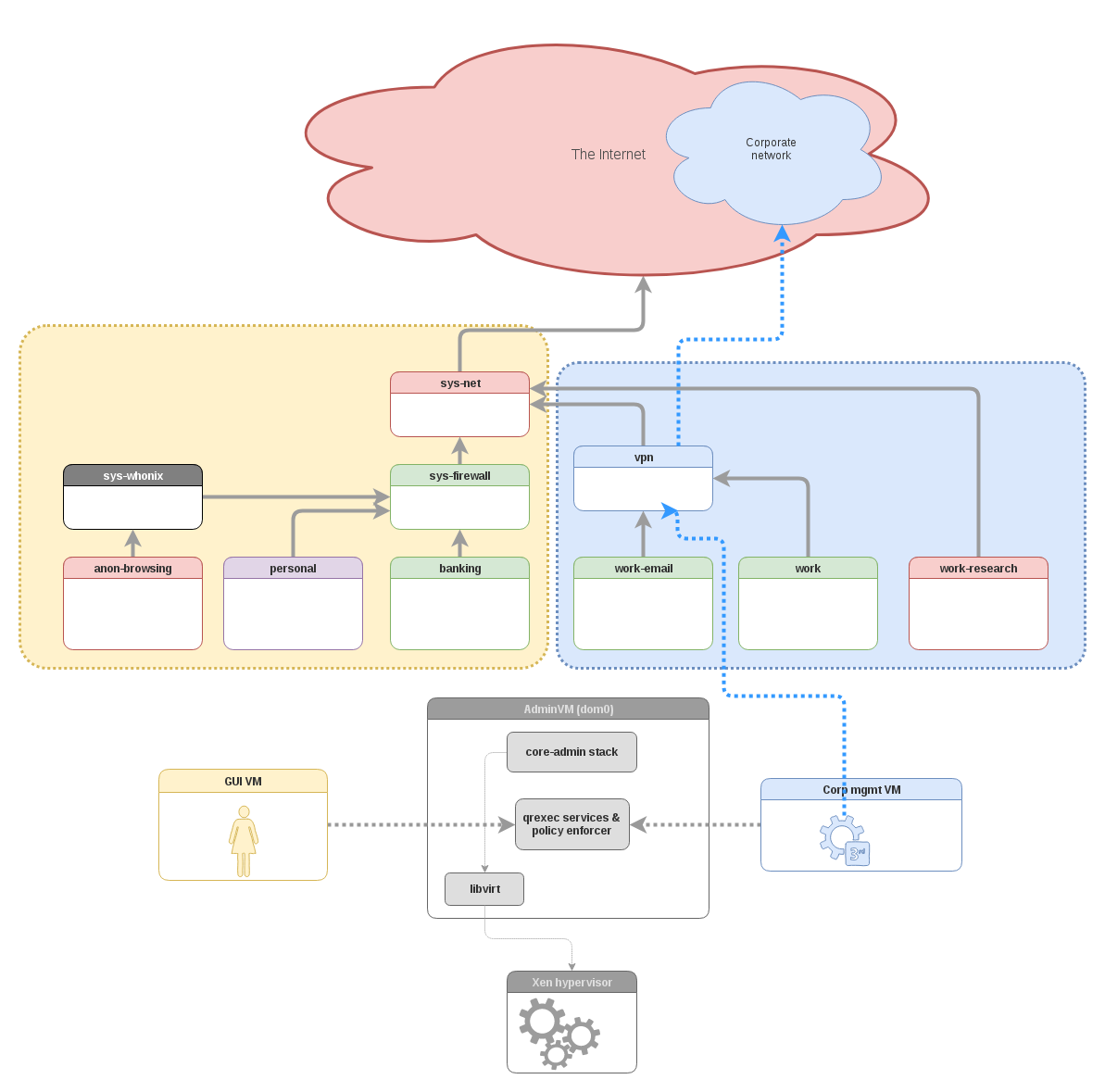
This post starts the “cool things coming in Qubes 4.0” series and focuses on what we call the “Qubes Admin API.” This should not be confused with Qubes Salt Stack integration, which we have already introduced in Qubes 3.2.
High-level overviewLet’s start with a high-level architecture picture of how the Admin API fits into the Qubes OS architecture:
As we can see, the main concept behind the Admin API is to let select VMs preform various select administrative functions over the Qubes OS system.
If this idea scares the hell out of you, then, my dear reader, we’re on the same side. Indeed, if we’re not careful, we...
Дожили: за 2016 год количество утекших данных приблизилось к численности населения России

Мы неоднократно подчеркивали, что картина утечек данных из российских организаций стремительно приближается к общемировой. Это связано со схожестью объектов защиты (типов используемых данных), ростом ценности информации и увеличением числа каналов передачи данных.
В 2016 году в СМИ обнародовано 213 случаев утечки информации из российских компаний и государственных органов, что составляет 14% от числа утечек данных по всему миру.
Чаще всего в России утекают персональные данные и платежная информация. На эти типы данных приходится 80% утечек, случившихся в 2016 году.
В 68% случаев виновными в утечке информации оказались сотрудники компаний. В 8% случаев — руководство организаций.
В 2016 году в России наибольшие доли утечек...
Compromise recovery on Qubes OS: individual VMs & full system cases
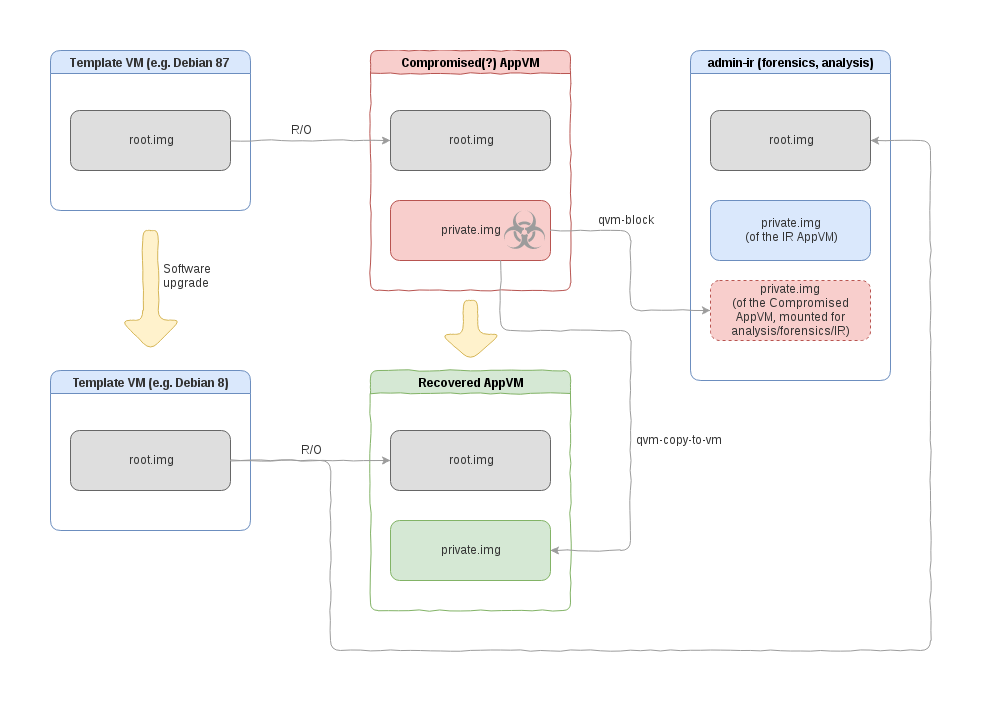
Occasionally fuckups happen, even with Qubes (although not as often as some think).
What should we – users or admins – do in such a situation? Patch, obviously. But is that really enough? What good is patching your system if it might have already been compromised a week earlier, before the patch was released, when an adversary may have learned of the bug and exploited it?
That’s an inconvenient question for many of us – computer security professionals – to answer. Usually we would mutter something about Raising the Bar(TM), the high costs of targeted attacks, attackers not wanting to burn 0-days, or only nation state actors being able...
Переход на личности: что такое identity theft

На безопасность персональных данных граждан не влияет ни политический режим в стране, ни уровень ее экономического развития. Обычным делом становится так называемая «кража личности». Что это такое? Откуда возник этот термин, какие самые громкие случаи кражи личности происходили за последние годы, а также - чего стоит бояться российским футбольным болельщикам уже в ближайшее время - обо всем этом читайте в нашей аналитической заметке.
Кража личности (англ. Identity theft — термин впервые появился в 1964 году) — преступление, при котором незаконно используются персональные данные человека для получения материальной выгоды.
Согласно опросам, кража личности является одним из основных опасений граждан США. В Соединенных Штатах...
Мощный всплеск: число утечек за год в РФ выросло на 80%

InfoWatch представляет свежий отчет об утечках во всем мире за 2016 год. Главное: российских утечек стало больше на 80%; РФ остается на 2-м месте в мире по их числу после США.
Полную версию отчета скачивайте по ссылке https://goo.gl/uLJ2zT
Какой вывод можно сделать по утечке ЦРУ?

7 марта 2017 года организация WikiLeaks начала публикацию секретного архива документов Центрального разведывательного управления (ЦРУ) США. Проект «Vault 7» должен стать крупнейшей утечкой конфиденциальных бумаг ведомства.
Аналитики InfoWatch разобрали публикацию утечки WikiLeaks с разных сторон: о каком ущербе может идти речь; какими реальными возможностями располагают в ЦРУ; что думают об этом участники нового шпионского скандала и главное – какие выводы нужно сделать из этой истории. Подсказка: как часто бывает, думать слишком хорошо о людях бывает опасно. Читайте по ссылке https://goo.gl/ZMVS8g
Как это работает: как устроена система приоретизации заявок в сервисных подразделениях.

Представьте. Вы обратились за помощью в службу поддержки компании X. Но эти ребята как будто не замечает ваших просьб о помощи, по телефону с ними не связаться, письма остаются без ответа. Знакомо? С чем могут быть связаны подобные проблемы, и имеет ли это отношение к нерациональному распределению ресурсов в сервисных подразделениях и неправильной приоритезации обращений заказчиков? Устраивайтесь поудобнее, сегодня вы узнаете, как работает система приоретизации заявок в сервисных подразделениях!
Мы рассмотрим основные критерии повышения или понижения приоритета обращения в службу технической поддержки, механику их работы, рассмотрим в каком порядке выстраиваются заявки для сотрудников и их непосредственных руководителей.
По воле случая: что меняется в мире данных
Однажды Директор спросил почтенного защитника Иня про защиту от внутренних угроз. Тот сказал:
– Внутренний враг бывает злонамеренный и неосторожный. Неосторожный враг подобен каплям дождя, что многочисленны и летят по воле ветра. От дождя легко заслониться зонтом. Злонамеренный враг подобен комару, который кусает в незащищённое место. Заслониться от него зонтом нельзя.
Директор ещё спросил:
– А какой инсайдер хуже, злонамеренный или неосторожный?
Инь Фу Во ответил:
– Нельзя так ставить вопрос. Оба они хуже.
Недавно наши аналитики решили провести первое сравнительное исследование большого объема данных по утечкам за 3 года - с 2013 по 2015 гг.
Коллеги хотели выяснить, как изменился характер инцидентов - в первую очередь...
Как визуализировать утечки: пример с архивом Хилари
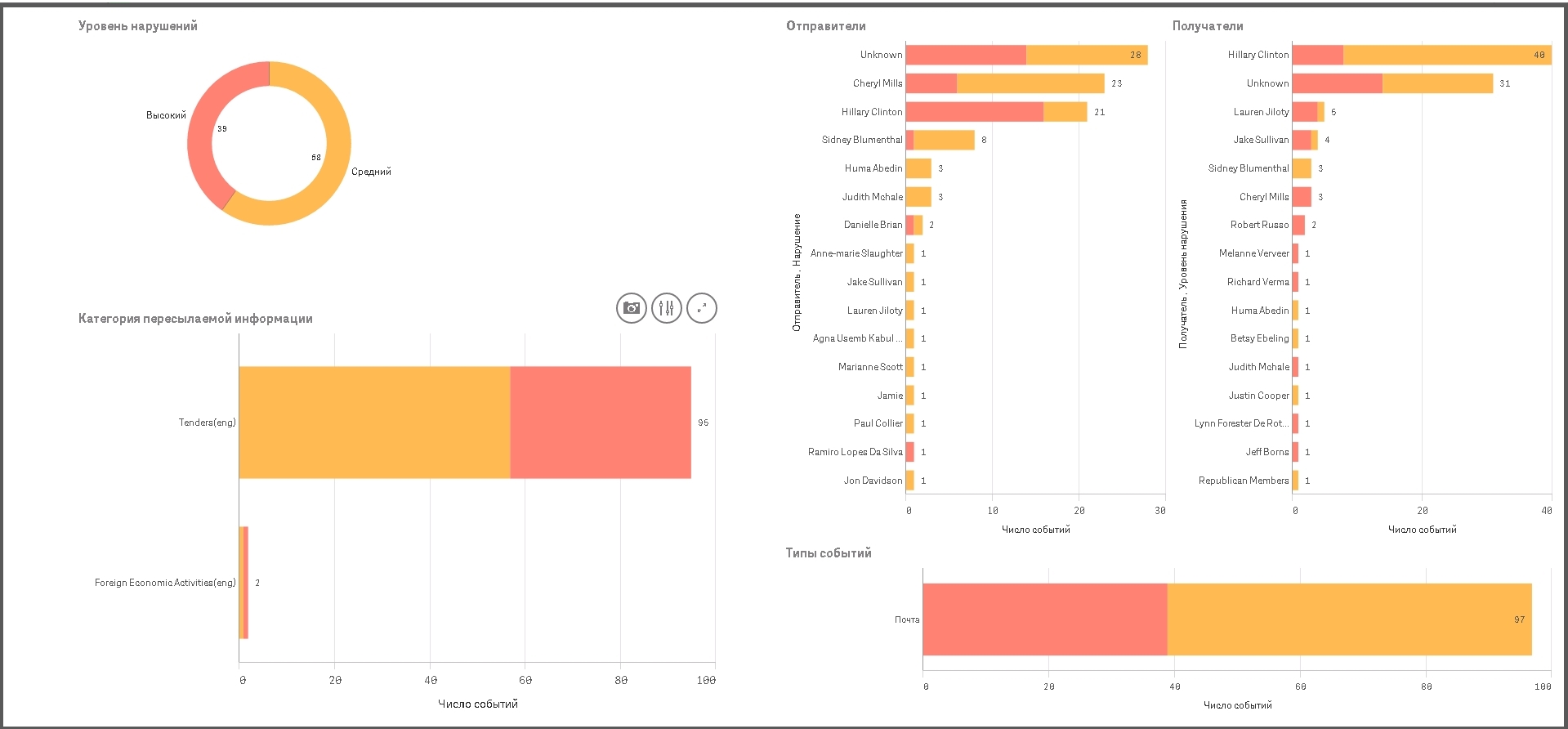
Недавно мы провели анализ 8000 писем Клинтон их архива госдепа США.
Если кратко:
более 7,500 писем содержали информацию о персональных данных
более 900 сообщений финансовую информацию
более 500 отправлений с юридическими данными
чуть менее ста писем с информацией о закупках и управлении персоналом HR
...Ну и заодно решили весь этот объем данных визуализировать с помощью нового продукта InfoWatch Vision.
Вот что у нас получилось.
Больше всего писем с предположительно конфиденциальными данными циркулировали в частной переписке между пятью людьми. Помимо самой Хиллари Клинтон, это ее помощница, адвокат и бывший советник по международной политике на посту Госсекретаря США Черил Миллс (Cheryl Mills), старший политический советник ее избирательной кампании...
Как это работает: учимся создавать свой sandbox с нуля: часть II

В первой части статьи вы получили краткое представление о драйверах в привилегированном режиме. Настало время покопаться в нашей песочнице.
Пример песочницы: сборка и установка драйвера
Ядром нашей песочницы является драйвер мини-фильтр. Вы можете найти его исходный код в src\FSSDK\Kernel\minilt. Я предполагаю, что вы используете комплект WDK 7.x для сборки драйвера. Чтобы сделать это, вы должны запустить соответствующее окружение, скажем, Win 7 х86 checked, и перейти в каталог с исходным кодом. Просто напишите «build /c» в командной строке при запуске в среде разработки и вы получите построенные драйверы. Для установки драйвера достаточно скопировать файл *.inf в папку, содержащую файл *.sys, перейти в этот...