Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
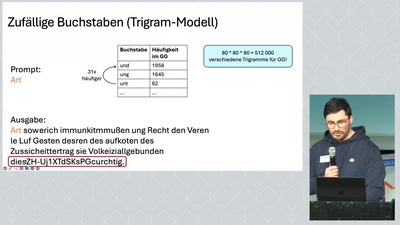
Wie funktioniert ChatGPT? (jh26)
Licensed to the public under https://creativecommons.org/licenses/by/4.0/
about this event: https://c3voc.de
Video:jh26rn-177-deu-Wie_funktioniert_ChatGPT_hd.mp4
Sim Swap Attacks Surging
SIM swap attacks are skyrocketing. A SIM Swap attack is when cybercriminals hijack mobile numbers by convincing carriers to transfer a victim’s phone number to a SIM card they control. Once successful, attackers intercept text-based authentication codes, unlocking access to cryptocurrency wallets, banking apps, and social media accounts.
The post Sim Swap Attacks Surging appeared first on Purism.
BugTraq.Ru: Notepad++ полгода раздавал зараженные обновления
С июня 2025 года взломанный хостинг популярного редактора Notepad++ перехватывал запросы на автообновление, перенаправляя их на вредоносные серверы, откуда уже приходил затрояненный инсталлятор в формате NSIS. Ситуацию усугубило отсутствие надежной проверки получаемых обновлений (в частности, использование самоподписанного корневого сертификата, открыто лежащего на GitHub).
Хостер устранил взлом 2 сентября, но взломщики сохраняли возможность перенаправлять трафик до 2 декабря.
Предположительно взлом является точечным и не направлен на рядовых пользователей (так себе утешение), среди мишеней называются "телекоммуникационные и финансовые компании восточной Азии".
Признаками заражения могут быть:
- подозрительная активность процесса gup.exe, отправляющего запросы куда-нибудь помимо notepad-plus-plus.org;
- файлы AutoUpdater.exe либо update.exe во временном каталоге;
- каталог %AppData%\Bluetooth, содержащий в...
I have a new blog: Traces of Humanity!
Hello! Welcome back! After all those years of silence, I’ve felt like writing a blog again :-)
But these days I no longer do computer security – other topics interest me more now. Thus, I have spun up a new blog titled: Traces of Humanity.
It is mainly intended to be a reportage of my struggles between Rationality and Humanism. Plus a place to discuss some of my new projects :-) I discuss this more in the short intro post.
You can follow using your favorite RSS client, or – new for this edition! – as an email-based newsletter.
See you there!
joanna.
Winterchaos in Chemnitz am 7.2.2026
TL;DR 7.2.2026 im Lokomov (Augustusburger Straße 102, Chemnitz) Vorträge, Lightning Talks, Workshops (tbd.) und Abendunterhaltung chch.it/Winterchaos; CfP inzwischen geschlossen
Am 7. Februar laden wir euch nach Chemnitz zum gemütlichen Winterchaos ein. Zwischen Retro-Computern, Waffeln und USB-C-Schnittstellen treffen wir uns im Lokomov in der Augustusburger Straße 102 zu einem Nachmittag und Abend mit Vorträgen, Lightning Talks und etwas Abendunterhaltung. Bei Gelegenheit könnt ihr außerdem unseren Hackspace besuchen.
Anmeldung:Die Teilnahme ist kostenlos, aber eine Anmeldung unter tickets.chch.it/ChCh/Winterchaos2026/ hilft uns zu planen!
CfP (Call for Participation) – inzwischen geschlossenAnmerkung des Eventblog-Teams: Durch verspätete Bearbeitung dieser Einreichung veröffentlichen wir diesen Blogeintrag leider zu spät für den Call for Participation, er...
Погружение в пиксели: знакомство с ZX Spectrum

В последние январские деньги, пока праздничное настроение начала года ещё не окончательно уступило место унылым трудовым будням, я решил затронуть одну лёгкую, едва ли познавательную и откровенно ностальгическую тему. Расскажу про своё первое близкое знакомство с компьютерами и играми. Своего рода мемуары, или, как говорит один известный игровой ретро-блогер, «Memories». Помимо личной истории и отсылок к различным приметам эпохи, это будет обзор шести случайных игр, с которыми мне довелось тогда столкнуться.
Читать далееUnabhängig von Mapbox und Co mit selbst gehosteten interaktiven Karten (niam2026)

In den letzten Monaten habe ich beim SPIEGEL ein Setup auf Basis von MapLibre und Protomaps aufgebaut. Im Talk gebe ich einen Einblick in den Workflow, zeige wie wir Karten auf Basis von umfangreichen Datensätzen erstellen, und wie daraus standardisiert ein interaktives Scrollytelling wird. Interaktive Karten sind aus der digitalen Berichterstattung des SPIEGEL nicht mehr wegzudenken – sie machen komplexe Themen anschaulich und räumliche Daten zugänglich. Bis vor Kurzem waren wir dafür jedoch auf kostspielige Drittanbieter angewiesen. Inzwischen setzen wir auf einen eigenen Open-Source-Kartenstack auf Basis von Protomaps und MapLibre. Das spart uns nicht nur tausende Euro...
Visuelle Wissenschaftskommunikation für die Archäologie (niam2026)

Wie lassen sich anhand von animierten und interaktiven Karten visuelle Geschichten erzählen und für die Wissenschaftskommunikation einsetzen? Archäologische Funde auf Amrum werden durch multimediale Inszenierung lebendig: Heute gestern erleben. Forscher:innen des Exzellenzclusters ROOTS der Christian-Albrechts-Universität zu Kiel sind auf der Nordseeinsel Amrum auf sensationelle Funde historischer Siedlungen aus der Wikingerzeit gestoßen. In Kooperation mit den Wissenschaftler:innen entwickelten Master-Studierende im Studienschwerpunkt Interaktives Informationsdesign der Muthesius Kunsthochschule 3D-Visualisierungen, um Grabhügel, Häuser und Wallungen zu rekonstruieren, zu erklären und über interaktive und animierte Karten erlebbar zu machen. Ein infografisches Beschilderungskonzept vor Ort, eine mobile 3D-Karthografie-App zur Navigation zu...
Wie schnell ist das nächste Krankenhaus erreichbar? - Ein interaktives Tool für den (Lokal-)Journalismus (niam2026)

Das neue Krankenhausgesetz (KHVVG) verändert die Kliniklandschaft. Auf Grundlage einer bundesweiten 100×100m-Raster Erreichbarkeitsanalyse ermöglicht unser Tool daten- und lokaljournalistischen Redaktionen, Versorgungsszenarien flexibel zu simulieren und ihre Recherchen datenbasiert zu vertiefen. Die Krankenhauslandschaft befindet sich in einem ständigen Wandel. Während politische Debatten oft auf die bundes- oder landesweite Versorgung fokussieren, ist für die meisten Menschen die Erreichbarkeit von Kliniken vor Ort entscheidend. Unser Tool richtet sich an Daten- und Lokaljournalist*innen und ermöglicht es, Versorgungsszenarien exakt zu analysieren: Wie lange dauert die Fahrt zur nächsten Klinik? Welche Fahrzeitveränderungen ergeben sich, wenn Kliniken mit weniger als 500 Geburten...
GeoTIFF DEM als 3D-Modell (niam2026)

Ich gebe einen kurzen Einblick, wie ich einen Open-Source-Workflow entwickelt habe, um das Copernicus-DEM für eine beliebige Region herunterzuladen und anschließend in ein 3D-druckbares Geländemodell zu konvertieren. Das [Copernicus DEM - Global and European Digital Elevation Model](https://dataspace.copernicus.eu/explore-data/data-collections/copernicus-contributing-missions/collections-description/COP-DEM) stellt weltweit ein Höhenmodell als GeoTIFF bereit, ich habe mich gefragt, wie ich für einen beliebigen Ausschnitt die GeoTIFFs herunterladen kann und basierend darauf das Höhenmodell als 3D-Modell drucken kann. Im Vortrag erkläre ich kurz meine Herangehensweise, die Auswahl der Technologien und wie ich die Skripte entwickelt habe. Der [Workflow ist open source](https://codeberg.org/stroebjo/dem-to-stl) und enthält folgende Schritte: - Download des DEMs...