Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
Verschlüsselung brechen durch physischen Zugriff - Smartphone Beschlagnahme durch Polizei (39c3)

Eine zwar profane Methode der Überwachung, die Polizeibehörden in Deutschland jedoch hunderttausendfach anwenden, ist das Auslesen von Daten beschlagnahmter Smartphones und Computer. Dazu nutzt die Polizei Sicherheitslücken der Geräte mithilfe forensischer Software von Herstellern wie Cellebrite oder Magnet aus. Die Verfassungsmäßigkeit der Rechtsgrundlagen ist zweifelhaft. Im Vortrag werden anhand aktueller Fälle technische und juristische Hintergründe erörtert. Staatstrojaner, Chat-Kontrolle, Wanzen. Die Mittel staatlicher Überwachung sind vielfältig und teilweise technisch sehr komplex. Dabei ist es leicht, den Überblick zu verlieren. Ein relativ profanes Mittel, das Polizeibehörden in Deutschland hunderttausendfach anwenden, ist die Beschlagnahme von Smartphones und Laptops...
How to keep Open Source open without leaving our communities open to threats (39c3)

The Four Freedoms (defined ~40 years ago) and the Four Opens (~15 years ago) for Open Source provided canonical definitions for what are the cornerstones of Open Source Software communities today. While the ethos still applies today, the cultural norms that blossomed to put it into practice are from an era with different challenges. To build a better world, we need to both keep and protect the value system of the Four Freedoms and Four Opens. To do that, we need to re-assess our risk and threat models to balance that allows beautiful minds to...
39C3: Power Off zur Abreise!
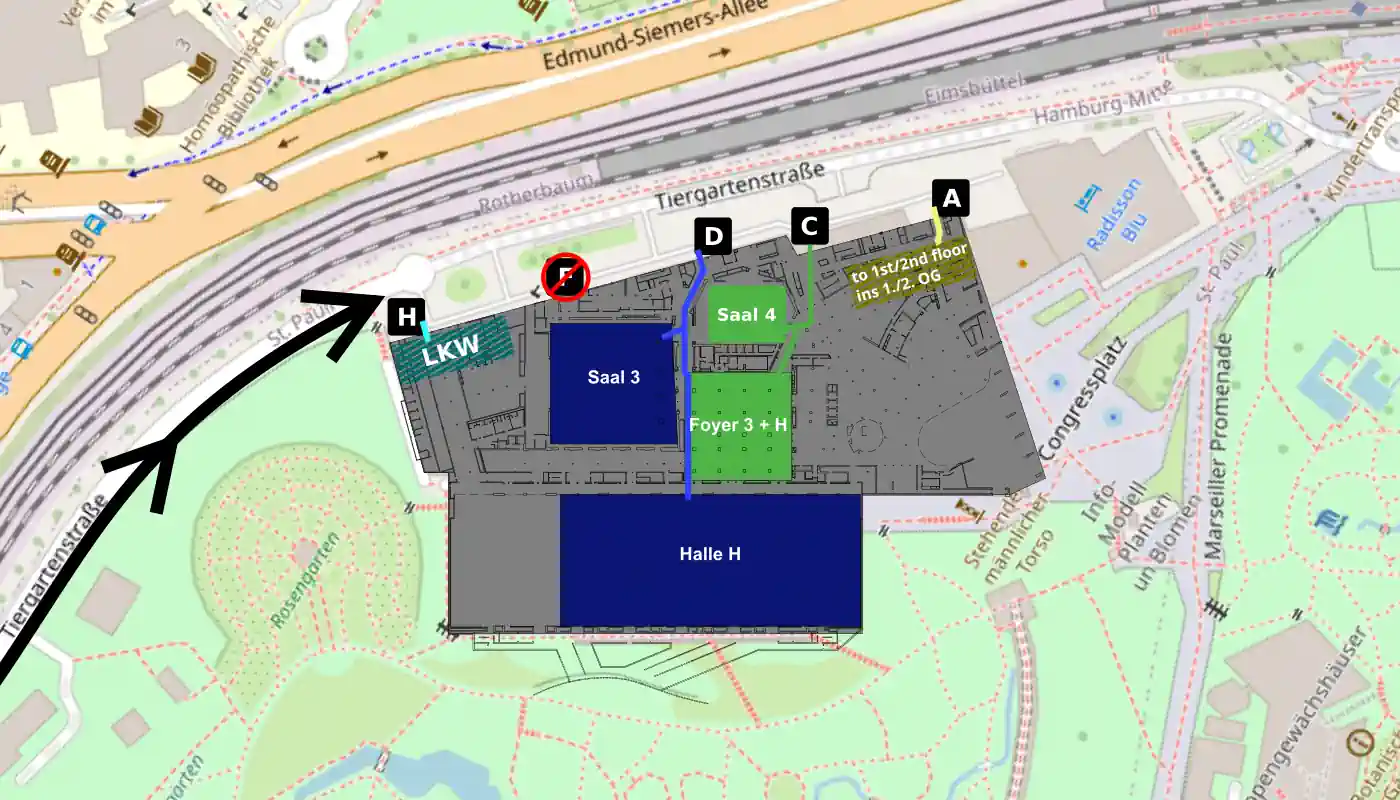
Liebe Wesen und Teilnehmende,
das Ende ist nahe! Tage voller Begegnungen, Neugier, Lötzinn, Diskurs, Musik, Code und Chaos liegen hinter uns. Danke, dass ihr diesen Congress mit Leben gefüllt habt. Ihr habt ihn zu dem gemacht, was er ist.
So sehr wir uns wünschen, dass der Congress ewig weiterläuft, kommt nun der Moment des Zusammenpackens, Durchatmens und Abschiednehmens.
Nach dem Closing beginnen die Assemblies damit, ihre Räume wieder zu leeren. Bitte nehmt euch die Zeit, ordentlich und achtsam abzubauen. Räumt möglichst schnell eure Tische frei, damit das Möbelhaus Tische und Stühle abtransportieren kann und Netzwerk und Strom abgebaut werden können. Die Hardware für...
Build a Fake Phone, Find Real Bugs (39c3)

Mobile phones are central to everyday life: we communicate, entertain ourselves, and keep vast swaths of our digital lives on them. That ubiquity makes high-risk groups such as journalists, activists, and dissidents prime targets for sophisticated spyware that exploits device vulnerabilities. On Android devices, GPU drivers have repeatedly served as the final escalation vector into the kernel. To study and mitigate that risk, we undertook a research project to virtualize the Qualcomm Android kernel and the KGSL graphics driver from scratch in QEMU. This new environment enables deep debugging, efficient coverage collection, and large-scale fuzzing...
FAFO: How we stopped worrying and bought an Electron Microscope (39c3)

We went on Kleinanzeigen and started a non-profit semiconductor lab.
We created a space to do the kind of research we've always wanted, but couldn't do at our local hackerspaces - either due to space constraints, or lack of structures allowing for a safe operation of a proper lab.
--
This video was independently recorded & produced by dmi
about this event: https://events.ccc.de/congress/2025/hub/en/event/detail/fafo-how-we-stopped-worrying-and-bought-an-electro
Video:import-56511-eng-FAFO_How_we_stopped_worrying_and_bought_an_Electron_Microscope_hd.mp4
The Heartbreak Machine: Nazis in the Echo Chamber (39c3)

WhiteDate ist eine Plattform weißer Suprematist:innen, die sich an Rassist:innen und Antisemit:innen richtet – und auf veralteter Infrastruktur basiert. Was die 8000 Mitglieder nicht wussten: Einige der Nazis flirteten dieses Jahr mit realistisch wirkenden Chatbots - und verliebten sich sogar in sie. Mit einer Kombination aus automatisierter Konversationsanalyse, Web-Scraping und klassischen OSINT-Methoden verfolgten wir öffentliche Spuren und identifizierten die Personen hinter der Seite. Dieser Vortrag zeigt, wie KI-Personas und investigatives Denken extremistische Netzwerke aufdecken und wie Algorithmen gegen Extremismus eingesetzt werden können. Monatelang tauchte Martha in die verborgene Welt von WhiteDate, WhiteChild und WhiteDeal...
The Spectrum - Hackspace Beyond Hacking (39c3)

The Spectrum is a newly founded queer-feminist, intersectional hackspace centering FLINTA+, disabled, and marginalized beings. We see hacking as playful exploration—of technology, art, and ideas—to reimagine what inclusion and collaboration can be. At 39C3, we share how awareness, accessibility, and transdisciplinary creation can transform community and hack the norm. The Spectrum is a new queer-feminist, intersectional and transdisciplinary hackspace centering FLINTA+, creatures with disabilities, and other marginalized communities founded in 2025. We see hacking as more than code and machines—it’s a way of exploring the world through curiosity, play, and care. By taking things, systems,...
Race conditions, transactions and free parking (39c3)

ORM's and/or developers don't understand databases, transactions, or concurrency. After the [Air France-KLM dataleak](https://media.ccc.de/v/37c3-lightningtalks-58027-air-france-klm-6-char-short-code) I kept repeating this was not a real hack, and confessed I always wanted to hack a system based on triggering race conditions because the lack of proper transactions. This was way easier than expected. In this talk I will show how just adding `$ seq 0 9 | xargs -I@ -P10 ..` can break some systems, and how to write safe database transactions that prevent abuse. In this talk I will explain what race conditions are. Many examples of how and why...
Light in the Dark(net) (39c3)

Science is hard and research into the usage of the Tor network is especially so. Since it was designed to counter suveillance, it gathering reliable information is difficult. As a consequence, the studies we do have, have yielded very different results. This talk investigates the root causes of contradicting studies by highlighting how slight changes in methodology or data selection completely change the results and thereby our understanding of what the Darknet is. Whether you consider it the last bastion of freedom or a haven of crime, this talk will tell you where to look...
Block Domains and Advertisements in a ZTE DSL Router

In one of my previous blog posts I showed how to install and run PiHole DNS server locally as a Docker container in your Synology NAS server. This worked great as the PiHole dashboard shows the list of identified annoying advert requests that were blocked shows.
So far I did configure my PiHole DNS server within my Chrome browser so that the browser cant load those annoying domains anymore. This worked like a charm, until quite recently Google updated Chrome browser to only allow a ‘secured DNS connection’ which actually seems a bit of a trojan horse for their own ads...