Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
Schlechte Karten - IT-Sicherheit im Jahr null der ePA für alle (39c3)

Seit Mitte 2025 steht die elektronische Patientenakte für alle zur Verfügung – nach ein paar kleineren oder größeren Sicherheitsproblemen im Vorfeld, sei es vor einem Jahr auf dem 38C3 oder Ende April zum deutschlandweiten Start. Zeit ein Fazit zu ziehen: Ist die ePA jetzt sicher? Wurden nachhaltige Veränderungen durchgeführt, die zu mehr Sicherheit führen? Kann der Umgang mit der IT-Sicherheit «eines der größten IT-Projekte der Bundesrepublik» für zukünftige Digitalprojekte hilfreich sein? Zeit, mit etwas Abstand auf das zu blicken, was war, was ist und was sich abzeichnet nicht nur bei der ePA, sondern auch beim...
Learning from South Korean Telco Breaches (39c3)

2025 was a bad year for South Korean mobile network operators. All three operators (SK Telecom, KT, LG U+) were affected by breach in some part of their respective network: HSS of SK Telecom, femtocells of KT. Meanwhile, handling of the breach by each operators and post-mortem analysis of each breaches have stark differences. The technical details and implemented mitigations are often buried under the vague terms, and occasionally got lost in translation to English. In this talk, I will cover the technical aspects of SK Telecom and KT's breach, and how the operators...
Netzpolitik in der Schweiz: Zwischen Bodensee und Matterhorn (39c3)

Auch in der Schweizer Netzpolitik ging es im auslaufenden Jahr drunter und drüber. Wir blicken mit gewohntem Schalk auf das netzpolitische Jahr 2025 zwischen Bodensee und Matterhorn zurück - und diskutieren jene Themen, die relevant waren und relevant bleiben. **Themen sind unter anderem:** **E-ID und E-Collecting:** Die netzpolitische Community hat nicht nur eine privatisierte E-ID verhindert sondern auch den Datenschutz als zentrales Prinzip verankert und einen beispielhaften Gesetzgebungsprozess begleitet. Das Gleiche haben wir bei E-Collecting vor, mit dem wir die direkte Demokratie der Schweiz auf ein neues Level heben wollen. **Elektronisches Gesundheitsdossier:** Was macht man, um eine...
The Spectrum - Hackspace Beyond Hacking (39c3)

The Spectrum is a newly founded queer-feminist, intersectional hackspace centering FLINTA+, disabled, and marginalized beings. We see hacking as playful exploration—of technology, art, and ideas—to reimagine what inclusion and collaboration can be. At 39C3, we share how awareness, accessibility, and transdisciplinary creation can transform community and hack the norm. The Spectrum is a new queer-feminist, intersectional and transdisciplinary hackspace centering FLINTA+, creatures with disabilities, and other marginalized communities founded in 2025. We see hacking as more than code and machines—it’s a way of exploring the world through curiosity, play, and care. By taking things, systems,...
Hacking Karlsruhe - 10 years later (39c3)
"Wir gehen nach Karlsruhe!“ – das klang vor zehn Jahren nach Aufbruch und juristischem Hack. Heute ist klar: Strategische Prozessführung ist kein Sprint, sondern ein zähes, manchmal frustrierendes Dauerprojekt. In diesem Talk ziehen wir Bilanz: Was haben wir mit zivilgesellschaftlichen Verfassungsbeschwerden im Bereich Technologie erreicht – und wo sind wir gescheitert? Welche Fehler würden wir heute vermeiden, welche Wege waren richtig? Und was bedeutet es, wenn das höchste deutsche Gericht zunehmend weniger Lust auf digitalpolitische Grundrechtsfragen zeigt? Ein realistischer Blick hinter die Kulissen strategischer Klagen – und die Frage: Wie hackt man das Rechtssystem im Jahr...
Rowhammer in the Wild: Large-Scale Insights from FlippyR.AM (39c3)
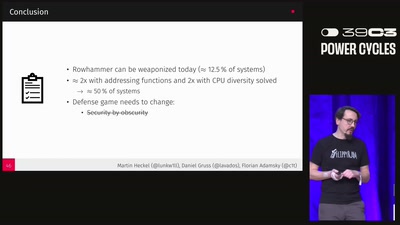
Last year at 38c3, we gave a talk titled "Ten Years of Rowhammer: A Retrospect (and Path to the Future)." In this talk, we summarized 10 years of Rowhammer research and highlighted gaps in our understanding. For instance, although nearly all DRAM generations from DDR3 to DDR5 are vulnerable to the Rowhammer effect, we still do not know its real-world prevalence. For that reason, we invited everyone at 38c3 last year to participate in our large-scale Rowhammer prevalence study. In this year's talk, we will first provide an update on Rowhammer research and present our results from that...
Block Domains and Advertisements in a ZTE DSL Router

In one of my previous blog posts I showed how to install and run PiHole DNS server locally as a Docker container in your Synology NAS server. This worked great as the PiHole dashboard shows the list of identified annoying advert requests that were blocked shows.
So far I did configure my PiHole DNS server within my Chrome browser so that the browser cant load those annoying domains anymore. This worked like a charm, until quite recently Google updated Chrome browser to only allow a ‘secured DNS connection’ which actually seems a bit of a trojan horse for their own ads...
OpenTelemetry Astroshop Simulator
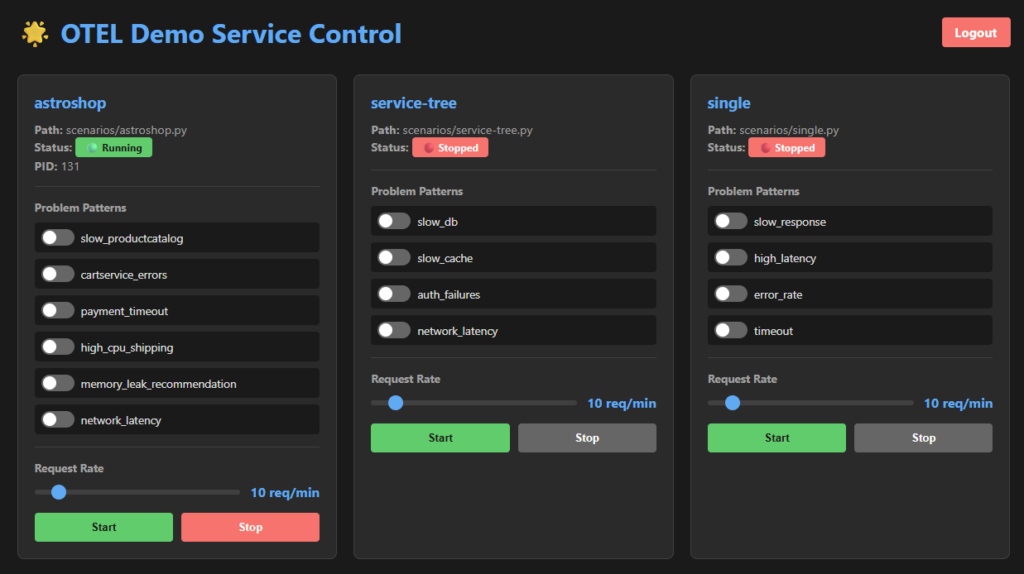
Astroshop is a great way of testing and running a demo scenario that offers with a large spectrum of technologies, services and a realistic problem scenario of running a real shop in serverless or Kubernetes infrastructure.
Besides, Astroshop being a great way to demo and test observability platforms such as Dynatrace and to run problem scenarios on demand, its also a bit cumbersome to deploy it for testing purposes. Imagine that you are a local developer that just needs to quickly run a test for a new feature using OTel traces and spans. Deploying Astroshop or any other scenario always comes...
51 Ways to Spell the Image Giraffe: (39c3)
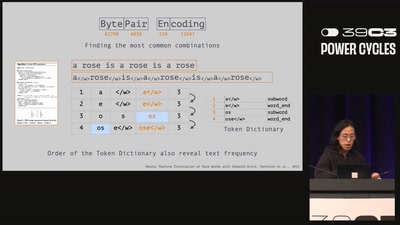
Generative AI models don't operate on human languages – they speak in **tokens**. Tokens are computational fragments that deconstruct language into subword units, stored in large dictionaries. These tokens encode not only language but also political ideologies, corporate interests, and cultural biases even before model training begins. Social media handles like *realdonaldtrump*, brand names like *louisvuitton*, or even *!!!!!!!!!!!!!!!!* exist as single tokens, while other words remain fragmented. Through various artistic and adversarial experiments, we demonstrate that tokenization is a political act that determines what can be represented and how images become computable through...
Machine Vision (39c3)
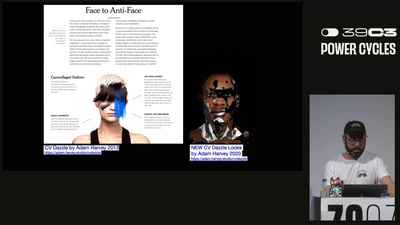
Milliarden von Kameras produzieren täglich Bilder, die zunehmend von Maschinen analysiert werden. In dieser Lecture Performance beleuchten wir die Entwicklung des maschinellen Sehens – von den frühen algorithmischen Ansätzen bis zu den heutigen Anwendungen – und schauen, wie verschiedene Künstler:innen diese Technologien nutzen und reflektieren. Anhand der beiden Arbeiten „Throwback Environment” und „Fomes Fomentarius Digitalis” betrachten wir die Nutzung des maschinellen Sehens in einem künstlerischen Feedback-Loop. Die Arbeiten machen sichtbar, was die eingesetzten Algorithmen sehen und in welchen Mustern sie operieren. Unmengen an Bilder werden Täglich in die Netzwerke hochgeladen. Doch nicht nur Menschen betrachten...