Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed Security (b)log [copy] http://securityblogru.livejournal.com/data/rss has loading error: cURL error 22: The requested URL returned error: 403 Forbidden
Feed [bodyawm] Богдан [copy] https://habr.com/ru/rss/users/bodyawm/articles/?fl=ru has loading error: cURL error 22: The requested URL returned error: 404
Denkangebot: Rainer Mühlhoff über KI und autoritäre Sehnsüchte im Silicon Valley (39c3)

Der Hype um künstliche Intelligenz ist allgegenwärtig. Selbst Donald Trump postet KI-generierte Videos, in denen er sich wahlweise als Rockstar oder Kampfjetpilot inszeniert. Elon Musk prahlte öffentlich damit, dass in seinem "Department of Goverment Efficiency" der soziale Kahlschlag mit Unterstützung Künstlicher Intelligenz vorangetrieben wird. Und Peter Thiel meint allen ernstes, KI-Regulierung und das Erscheinen des Antichristen gingen Hand in Hand. Müssen wir uns Sorgen machen? Rainer Mühlhoff ist Professor für Ethik und kritische Theorien der Künstlichen Intelligenz an der Universität Osnabrück. In seinem kürzlich erschienen Buch "Künstliche Intelligenz und der neue Faschismus" setzt er sich...
Race conditions, transactions and free parking (39c3)

ORM's and/or developers don't understand databases, transactions, or concurrency. After the [Air France-KLM dataleak](https://media.ccc.de/v/37c3-lightningtalks-58027-air-france-klm-6-char-short-code) I kept repeating this was not a real hack, and confessed I always wanted to hack a system based on triggering race conditions because the lack of proper transactions. This was way easier than expected. In this talk I will show how just adding `$ seq 0 9 | xargs -I@ -P10 ..` can break some systems, and how to write safe database transactions that prevent abuse. In this talk I will explain what race conditions are. Many examples of how and why...
Aber hier Leben? Nein danke! …oder doch? Wie wir der autoritären Zuspitzung begegnen können. (39c3)

Im Osten stehen nächstes Jahr schon wieder Wahlen an und schon wieder sieht alles danach aus, als ob die AfD eine Regierungsbeteiligung bekommen könnte. Ganz konkret: In Sachsen-Anhalt und Mecklenburg-Vorpommern. Nicht nur diese "rosigen" Aussichten, sondern auch aktuelle Bevölkerungsprognosen werfen gar kein günstiges Licht auf die Regionen. Linke Akteur:innen vor Ort kämpfen täglich dagegen an und sie brauchen unsere Solidarität. Wir müssen dem etwas entgegensetzen. Egal ob als Hacker:innen auf dem Congress oder Westdeutsche in (noch) Grünen Gemeinden. Wo kommt das alles her? Wer macht aktuell etwas dagegen und wie können wir dem rechten...
Human microservices at the Dutch Railways: modern architecture, ancient hardware? (39c3)

The Dutch railways have been operating an increasingly complicated network of trains for over 80 years. The task of overseeing it is far too complex for a single human. As such, a network of specifically scoped humans has been connected. Over time, computers and software have been introduced into the system, but today there is still a significant role for humans. This talk describes the network of "human microservices" that is involved in the Dutch Railways' day to day operation from the eyes of a software developer. When a train breaks down in the Netherlands, a...
Von Fuzzern zu Agenten: Entwicklung eines Cyber Reasoning Systems für die AIxCC (39c3)
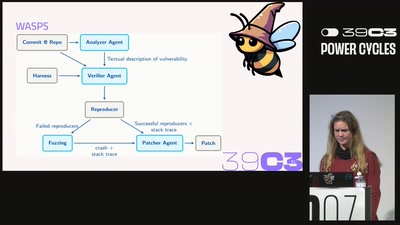
Die AI Cyber Challenge (AIxCC) der DARPA hatte zum Ziel, die Grenzen der autonomen Cybersicherheit zu erweitern: Können AI-Systeme Software-Schwachstellen unabhängig, in Echtzeit und ohne menschliche Hilfe identifizieren, verifizieren und beheben? Im Laufe von zwei Jahren entwickelten Teams aus aller Welt „Cyber Reasoning Systems“ (CRS), die in der Lage sind, komplexe Open-Source-Software zu analysieren, Code zu analysieren, reproducer zu generieren, um zu zeigen, dass ein gemeldeter Fehler kein Fehlalarm ist, und schließlich Patches zu synthetisieren. Unser Team nahm an dieser Challenge teil und entwickelte von Grund auf ein eigenes CRS. In diesem Vortrag geben wir Einblicke...
There is NO WAY we ended up getting arrested for this (Malta edition) (39c3)

3 years ago, 3 Maltese students were arrested and charged with computer misuse after disclosing a vulnerability to a local company that developed a mobile app for students. Through persistent media pressure, the students managed to obtain a presidential pardon to drop the case and funding for their lawyers. However, through this journey, there were mentions of punishment for retaliating through media disclosure. The story has not concluded, and there will be no amendments to the Maltese computer misuse law for the foreseeable future. The talk goes through the full journey, 1. The talk describes in...
Lightning Talks - Tag 3 (39c3)
Lightning Talks - Tag 3 - **Lightning Talks Introduction** - **"Oma, erzähl mir von der Zukunft" oder: Wie wir weiter interessante Sachen machen, ohne den Planeten zu ruinieren 🌱** — *EstherD* - **Don't abuse the ecosystem** — *michele* - **The Climatepoetry.org video tool** — *Magnus Ahltorp* - **Neo-Kolonialismus & Katzenbilder - Installation zur Lieferkette von GenAI** — *Stefan, Yannik & Rike* - **Build social inventories with StashSphere** — *Maximilian Güntner* - **Invitation to the Fermentation Camp "Kvas 2026"** — *algoldor* - **Stretching nginx to its limits: a music player in the config file** — *Eloy* - **2D Graphics Creation with Graphite -...
Gegenmacht - Best of Informationsfreiheit (39c3)

Sind mehr Infos wirklich die Lösung? Ob Jens Spahn, Philipp Amthor oder Friedrich Merz - sie alle sagen offen, was sie vorhaben und machen keinen Hehl aus ihren Verbindungen zur Trump-Regierung, zu Milliardären und der fossilen Lobby. Was bringt Transparenz in Zeiten der autoritären Wende? Transparenz braucht Rechenschaft. Ohne Konsequenzen bleibt Transparenz wirkungslos. Wie können wir also eine wirksame Gegenmacht schaffen, die Veränderungen durchsetzt? Philipp Amthors Angriff aufs Informationsfreiheitsgesetz konnten wir erst einmal abwehren - jetzt geht's in die Offensive! Mit den Highlights aus Strafanzeigen gegen Alexandeer Dobrindt, Spahns geleaktem Maskenbericht, der Milliardärslobby im Wirtschaftsministerium und...
GPTDash – Der Reverse-Turing-Test (39c3)
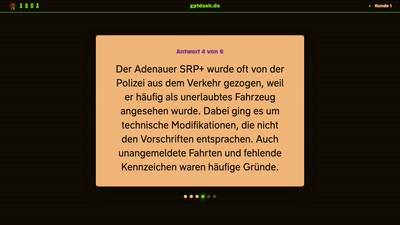
KIs (bzw. LLMs) wirken immer menschlicher. Schon längst ist es schwer bis unmöglich zu erkennen, ob ein Text von einer KI oder einem Menschen geschrieben wurde. Maschinen dringen immer mehr in den menschlichen Diskurs ein. Wir wollen das nicht länger hinnehmen und drehen den Spieß um. In unserem Reverse-Turing-Test schlüpfen die Teilnehmenden in die Rolle einer KI und versuchen so robotisch-menschlich wie möglich zu klingen. In einer anschließenden Blindstudie prüfen wir, wer sich am besten unter KIs mischen und beim nächsten Robot Uprising die Spionin der Wahl wäre. Humor, Kreativität und ein Hang zu allgemeingültigen, nichtssagenden...
Zellkultur (39c3)

Ich bin ja glaube ich reichlich spät, aber da Moepern endlich wieder zum Congress kommt und ich das erst vor kurzem erfahren habe, dachte ich, ich werfe unseren Namen mal in den Hut. Wir sind/waren ein Biologie-Podcast und durch Babypause bei Moepern ist der etwas eingeschlafen. Schaffen wir ein Revival? Verratet ihr's uns. Wir nehmen auch den Podcast-Tisch wenns sonst nicht passt. :) In der Zellkultur reden Claudia (moepern) und Anna (Adora Belle) über das Leben, die Biologie und den ganzen Rest. Am liebsten schauen wir tief in die Zelle, auf die DNA und schauen...