Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Verification of OS artifacts without stateful keyrings (asg2025)

Many OS artifacts today are still verified using proprietary, stateful keyring formats. With the "File Hierarchy for the Verification of OS Artifacts (VOA)" an attempt is made to rid the ecosystem of this limitation by implementing a generic lookup directory. With extensibility in mind, this unifying hierarchy currently provides integration for OpenPGP, with further integrations in planning. While working on improvements to the [ALPM](https://alpm.archlinux.page) ecosystem, the way packages and other OS artifacts are currently verified on Arch Linux has been evaluated. Noticing the extensive vendor lock-in to GnuPG and with today's widespread availability of [Stateless OpenPGP](https://wiki.archlinux.org/title/Stateless_OpenPGP) implementations in...
Extending Fedora Atomic Desktops using systemd system extensions (asg2025)
On image based desktops distributions such as Fedora Atomic desktops and Universal Blue, users are expected to run their graphical applications using Flatpaks and their command line ones using containers. But that approach does not work well for some applications that require more privileges, direct access to devices or kernel interfaces. With systemd system extensions (sysexts), it is possible to extend an image based system on demand. Sysexts come with a lot of advantages: they can be created out of arbitrary content (not only packages), are quickly enabled or disabled and can be built and...
From initramfs-tools to mkosi-initrd (asg2025)
Marco will review the features available in the initramfs-tools ecosystem, the initrd generator used by Debian and Ubuntu, and how they can be implemented (or not) by adopting mkosi-initrd.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/de/
about this event: https://cfp.all-systems-go.io/all-systems-go-2025/talk/E989ZX/
Video:asg2025-365-eng-From_initramfs-tools_to_mkosi-initrd_hd.mp4
Accessing shadow records via varlink (asg2025)
Provide a varlink service to access /etc/passwd and /etc/shadow so that no setuid and setgid binaries are necessary for this task. There are two independent "problems" which can be solved with the same idea: all files in /usr should be owned by root:root and no setuid binary should be needed. The first one is a requirement of image based updates of /usr to avoid UID/GID drift, the second one is a security feature wished by systemd developers and security teams. Currently most setuid binaries (or setgid binaries owned by group shadow) beside su and sudo only...
A new systemd container runtime?! (asg2025)

At Meta, we've been looking to revamp our internal container runtime (Twine). Instead of maintaining all the low level container runtime code ourselves, we'd much prefer having more of this managed by systemd. This talk will go over what we did to make systemd transient units a suitable environment for running system containers (pid namespace support, cgroup namespace support, namespace delegation, ...), and why we went this route instead of reusing systemd-nspawn.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/de/
about this event: https://cfp.all-systems-go.io/all-systems-go-2025/talk/BBTJSF/
Video:asg2025-342-eng-A_new_systemd_container_runtime_hd.mp4
Look ma, no secrets! - bootstrapping cryptographic trust in my homelab using Nix, UKIs, TPMs and SPIFFE (asg2025)
All the big cloud providers provide your machines with a unique cryptographic identity that can be used to talk to their cloud services securely without having to manage or rotate any cryptographic secrets yourself. For example GCP has Service accounts and AWS has IAM roles. This ubiquity of cloud identity and the seamless integration with all the the services of these cloud providers is one of the reasons why they are so successful. SPIFFE (Secure Production Identity Framework For Everyone) tries to unify these concepts of workload identity in a vendor neutral...
ParticleOS: Why is Lennart still not dogfooding systemd?! (asg2025)
More than six months have passed since Daan tried to ~~shame~~ gently peer pressure Lennart to actually use the stuff he builds, via a FOSDEM talk: https://fosdem.org/2025/schedule/event/fosdem-2025-4057-particleos-can-we-make-lennart-poettering-run-an-image-based-distribution-/ Did he succeed? Is dogfooding standard practice now in the systemd development process? Or do things like randomly breaking logging in GNOME (*cough*) still happen from time to time? Join us for this talk to find out, and to apply yet more peer pressure. We will also spend some time talking about more boring and mundane topics, such as giving an overview of the current status of ParticleOS, and how...
Systing: tracing for the lazy (asg2025)
Systing helps you solve problems in minutes rather than days. Out of the box it gives you everything you could possibly need, combined with perfetto’s visualization you will never be confused again. This talk will introduce systing, a tracer that is built on modern BPF tooling, purpose built to debug large applications with complicated interactions. This will be little talk and mostly demo. Two decades of experience debugging kernel problems has been poured into this tool to make it as straightforward as possible. I will walk through the basic usage, and show a case study investigation...
isd: interactive systemd (asg2025)
Simplify systemd management with `isd`! `isd` is a TUI offering fuzzy search for units, auto-refreshing previews, smart sudo handling, and a fully customizable interface for power-users and newcomers alike. If you ever became frustrated while typing: - `systemctl start --user unit-A.service` (manually starting a unit) - `systemctl status --user unit-A.service` (seeing that it failed) - `journalctl -xe --user -u unit-A.service` (checking the logs) - `systemctl edit --user unit-A.service` (updating the unit) - (repeat until problem is solved) `isd` could help. In this presentation, we will discuss the features that `isd` currently supports, the features that are planned for the future, and the...
Sandboxing services with Landlock (asg2025)
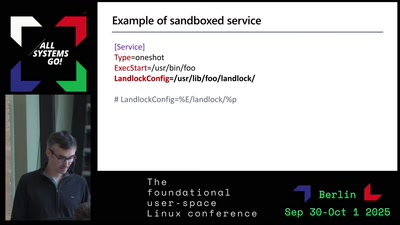
Landlock is an unprivileged kernel feature that enables all Linux users to sandbox their processes. Complementary to seccomp, developers can leverage Landlock to restrict their programs in a fine-grained way. While Landlock can be used by end users through sandboxer tools, there is currently no well-integrated solution to define security policies tailored to system services. Although AppArmor and seccomp security policies can already be tied to a system unit, we aim to provide a more dynamic, standalone, and unprivileged option with Landlock. In this talk, we'll briefly explain what Landlock is and highlight its differences...