Feed cleverhans-blog [copy] http://www.cleverhans.io/feed.xml has loading error: cURL error 22: The requested URL returned error: 404
Verification of OS artifacts without stateful keyrings (asg2025)

Many OS artifacts today are still verified using proprietary, stateful keyring formats. With the "File Hierarchy for the Verification of OS Artifacts (VOA)" an attempt is made to rid the ecosystem of this limitation by implementing a generic lookup directory. With extensibility in mind, this unifying hierarchy currently provides integration for OpenPGP, with further integrations in planning. While working on improvements to the [ALPM](https://alpm.archlinux.page) ecosystem, the way packages and other OS artifacts are currently verified on Arch Linux has been evaluated. Noticing the extensive vendor lock-in to GnuPG and with today's widespread availability of [Stateless OpenPGP](https://wiki.archlinux.org/title/Stateless_OpenPGP) implementations in...
Extending Fedora Atomic Desktops using systemd system extensions (asg2025)
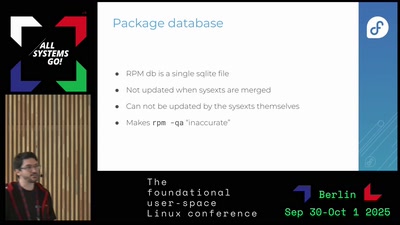
On image based desktops distributions such as Fedora Atomic desktops and Universal Blue, users are expected to run their graphical applications using Flatpaks and their command line ones using containers. But that approach does not work well for some applications that require more privileges, direct access to devices or kernel interfaces. With systemd system extensions (sysexts), it is possible to extend an image based system on demand. Sysexts come with a lot of advantages: they can be created out of arbitrary content (not only packages), are quickly enabled or disabled and can be built and...
From initramfs-tools to mkosi-initrd (asg2025)
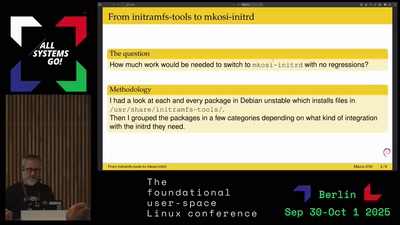
Marco will review the features available in the initramfs-tools ecosystem, the initrd generator used by Debian and Ubuntu, and how they can be implemented (or not) by adopting mkosi-initrd.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/de/
about this event: https://cfp.all-systems-go.io/all-systems-go-2025/talk/E989ZX/
Video:asg2025-365-eng-From_initramfs-tools_to_mkosi-initrd_hd.mp4
A Security Model for systemd (asg2025)

Linux lacks a coherent security model, and by extension we never defined one for the systemd project either. In this talk I'd like to start changing this, and begin defining some general security design guidelines that we so far mostly followed implicitly, and make them more explicit. After all, systemd to a large degree is involved in security subsystems, from SecureBoot, Measured Boot & TPM, to its service sandboxing, dm-verity/dm-crypt support, its FIDO2/PKCS#11 hookups, its many security boundaries, secure parameterization, Linux Security Module initialization and more. While this distributions & applications consuming systemd might follow different...
systemd-confext Two Years On: Versioned Overlays for /etc, Reloaded (asg2025)

systemd-confext is a lightweight overlay mechanism for /etc, allowing you to drop in a configuration extension ("confext") bundle and let systemd make it visible to your service as though it was already shipped with the base image. Building on the same extension magic as systemd-sysext, confext also introduces extra features tailored for the /etc use case, such as vpick-ing the newest version and the ability to pick up config revisions with a `systemctl reload`. This talk presents the changes to systemd-confext since [its debut at All Systems Go! 2023](https://cfp.all-systems-go.io/all-systems-go-2023/talk/XLQNDJ/), the lessons learned along the way...
Look ma, no secrets! - bootstrapping cryptographic trust in my homelab using Nix, UKIs, TPMs and SPIFFE (asg2025)
All the big cloud providers provide your machines with a unique cryptographic identity that can be used to talk to their cloud services securely without having to manage or rotate any cryptographic secrets yourself. For example GCP has Service accounts and AWS has IAM roles. This ubiquity of cloud identity and the seamless integration with all the the services of these cloud providers is one of the reasons why they are so successful. SPIFFE (Secure Production Identity Framework For Everyone) tries to unify these concepts of workload identity in a vendor neutral...
oo7-daemon: One year later – Progress, Challenges, and What’s next (asg2025)

oo7-daemon is the new D-Bus Secret Service provider that aims to fully replace gnome-keyring. In this followup (continuation of my 2024 talk) lightning talk, I will go through the progress made, the challenges faced and the status of systemd credentials integration.
Licensed to the public under https://creativecommons.org/licenses/by/4.0/de/
about this event: https://cfp.all-systems-go.io/all-systems-go-2025/talk/NFNFJS/
Video:asg2025-369-eng-oo7-daemon_One_year_later_-_Progress_Challenges_and_Whats_next_hd.mp4
Abusing Notion’s AI Agent for Data Theft
Notion just released version 3.0, complete with AI agents. Because the system contains Simon Willson’s lethal trifecta, it’s vulnerable to data theft though prompt injection.
First, the trifecta:
The lethal trifecta of capabilities is:
Access to your private data—one of the most common purposes of tools in the first place! Exposure to untrusted content—any mechanism by which text (or images) controlled by a malicious attacker could become available to your LLM The ability to externally communicate in a way that could be used to steal your data (I often call this “exfiltration” but I’m not confident that term is widely understood.)This is, of course, basically...
The Power of a Movement: Why Argentina in 2025 Is the Right Place for RWA
Crecimiento is here to prove what’s possible when talent, tech, and urgency collide in Argentina.
Vorträge, Musik, Kunst, Punk: Macht mit beim 39. Chaos Communication Congress!
Wir laden dazu ein, das Programm auf den Bühnen mit Vorträgen und den 39C3 mit Musik, Kunst und Punk zu bereichern. Der Call for Participation in gleich vier Feldern ist nun online.
Der Chaos Computer Club lädt Ende Dezember zum 39. Chaos Communication Congress nach Hamburg und bittet ab jetzt um Ideen für Vorträge. Die beste Hackerparty des Jahres könnt ihr außerdem mit euren Musik- und Kunstideen und mit Punk unterstützen.
Bitte lest unseren Call for Participation, bevor ihr eure Ideen einreicht. Denn hier finden sich praktische Hinweise und Handreichungen, um die eigene Einreichung am besten rüberzubringen und typische Fehler zu vermeiden.
Wir...