Feed linux for devices [copy] http://www.linuxfordevices.com/rss-feeds-1.xml has loading error: cURL error 22: The requested URL returned error: 404
Feed SparkFun Electronics [copy] http://www.sparkfun.com/feeds/news has loading error: cURL error 22: The requested URL returned error: 405
Feed The RFID Weblog [copy] http://www.rfid-weblog.com/index.rss has loading error: cURL error 22: The requested URL returned error: 404 Not Found
Hanjo: Der Wahnsinn mit der Geschwindigkeit

Warum zur Hölle wollen Menschen immer die Geschwindigkeit von Teams vergleichen?
Vielleicht weil der Begriff Geschwindigkeit dazu verleitet ein langsames Auto als Trabbi und ein schnelles als Porsche zu verbuchen. Dabei messen wir zwar immer das gleiche, nämlich in einem Sprint erledigte Arbeit. Die Maßeinheit sind in der Regel Storypunkte, welche aber keine über Teamgrenzen hinweg normierte Größe darstellen.
Das schmieren eines Brötchens kann von einem Team mit 1 Storypunkt geschätzt und von einem anderen mit 2 Storypunkten geschätzt werden, während ein drittes Team die Aufgabe die Aufgabe der Trivialität halber gar nicht schätzt. Jedes Team braucht am...
Hanjo: Gelobt ist auch Geschimpft
Ich habe meine Kinder nie geschimpft wenn sie schlechte Noten hatten. Ich gebe nicht viel auf Zahlen die unreflektiert und oft kontextfrei versuchen die Leistung von Menschen abzubilden. Und doch konnte ich immer wieder die Wirkung von Leistungsdruck spüren.
Vor Tests, Klassenarbeiten und mündlichen Kontrollen war sie da die Angst und Unsicherheit. Sorge es nicht zu können, zu viel berichtigen zu müssen, schlechter zu sein als die Klassenkameraden. Das gleiche vor dem Zeugnis, Angst vor der Drei auf dem Papier.
Natürlich spielt hier das direkte Lernumfeld eine Rolle. Der Lehrer als Person des Vertrauens gibt schließlich eine Wertung...
Hanjo: Erster Monat - Schule von Morgen

Hinter den großen Kindern liegt jetzt ein reichlicher Monat in einer neuen Universitätsschule Dresden. Einer Schule in der Alles und Alle neu sind. Alle müssen sich eingewöhnen, Kindergartenkinder die das erste Mal eine Schule besuchen, dazu Grund- und Oberschüler die vorher an anderen Einrichtungen beschult wurden. Aber nicht nur Kinder, auch Pädagogen müssen sich und das neue Konzept, Umgebung und Schüler kennenlernen.
Insgeheim haben wir natürlich, wie viele andere Eltern auch, auf eine fertige Schule gehofft. Mit fertigen Strukturen, Konzepten und wo alles flutscht. Dem ist aber nicht so und das ist in Ordnung.
All die Lücken im...
October Update: PineTime, Delays and Shipping News

This month’s update will be slightly shorter than usual - I have been dealing with some health issues recently, which significantly reduced my time to actively engage with the community. Hopefully I’ll make it up to you in November.
Public Health 2019, медицинская электроника
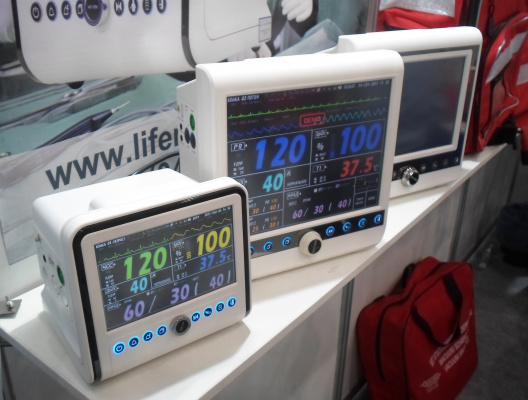
Вчера буквально утром узнал об интересной выставке и решил зайти.
Медицина касается нас всех, ну и лично я учился на разработчика именно приборов медицинского назначения.
Если вас тоже интересует подобная тема – ниже в статье выложил небольшое количество фотографий и кое-какие комментарии. :)
Читать дальше
Fake TL074 opamps - adventures in decapping

Fake greymarket parts, home chip decapping and a borrowed microscope.
Sometimes software development is a struggle
I'm currently working on the firmware for a new project, an 8-slot smart card reader. I will share more about the architecture and design ideas behind this project soon, but today I'll simply write about how hard it sometimes is to actually get software development done. Seemingly trivial things suddenly take ages. I guess everyone writing code knows this, but today I felt like I had to share this story.
Chapter 1 - IntroductionAs I'm quite convinced of test-driven development these days, I don't want to simply write firmware code that can only execute in the target, but I'm actually working on a USB CCID (USb...
Hanjo: Klimastreik Dresden 2019

Nun ist es schon wieder eine Woche her das in Dresden laut den Organisatoren etwa 14.000 Menschen im Rahmen des globalen Klimastreiktages auf die Straße gingen. Deutschlandweit waren es mehr als 1.4 Millonen. Aufgerufen zum Streik hatte unter anderem Fridays for Future. Wir waren mit einigen Kollegen ab dem Dresdner Hauptbahnhof ebenfalls dabei.
Die räumliche Nähe und der Start der Demo zur Mittagszeit hat mit Sicherheit dazu beigetragen das der eine oder andere eine verlängerte Mittagspause oder einen frühen Feierabend investiert hat.
Die Demo selbst war unspektakulär, wenn keine Nazis oder Fußballerspieler angekündigt sind, dann ist auch nicht...
Hanjo: Universitätsschule sucht Studierende

Die Universitätsschule ist ein Schulversuch, der neue Konzepte des Lernens in Schule erprobt. Die Schule ist eine Ganztagsschule und gelernt wird hauptsächlich in Projekten. Aktuell hat die Schule 200 Schüler*innen von der 1 bis zu 5. Klasse und wir suchen Studierende, die sich vorstellen können dieses Lernen sowohl in Projekten als auch in Werkstätten zu begleiten. Solltet Ihr/ Sie Interesse haben, freuen wir uns über eine Kontaktaufnahme. unischule@mailbox.tu-dresden.de
Лазерная резка металла: Первый опыт

Совсем недавно стала широко доступна крутая технология – CNC лазерная резка по металлу.
Я давно хотел её опробовать, и наконец – это свершилось!
В статье мы рассмотрим процесс создании чертежа, как происходит процесс заказа, ну и что же получилось из 3-х опробованных металлов: углеродистой стали, нержавеющей стали, и алюминия.
Скажу заранее – была допущена туча косяков, и заказать тоже было не просто. Поехали! :)
Читать дальше